
Introduction
Firewalls are a critical component of securing modern networks with internet access. Without firewalls in place, malicious actors could easily access and infect devices on a network. Properly configured firewalls substantially reduce undesirable communications.
This article explains how to create firewall rules using the Windows Firewall with Advanced Security console and Windows PowerShell on Windows Server 2016 / 2019 / 2022.
What is a Firewall?
A firewall controls the flow of data packets in and out of a network. It acts like a barrier, similar to how a physical firewall prevents the spread of fire between compartments. The firewall allows or blocks connections according to configured firewall rules.
Computers behind a firewall cannot receive data until it passes the filters. This greatly enhances security and reduces unauthorized access risks. Benefits of firewalls:
- Protect devices by blocking undesired traffic
- Notify administrators of connection attempts
- Log activity for monitoring
- Prevent spread of infections
- Reduce hacking risks
How Windows Server 2016 / 2019 / 2022 Firewalls Work
The Windows firewall acts as a barrier between local network devices and external networks. When a connection is attempted to a server, the firewall intercepts the traffic and evaluates it against the defined rules.
Only network packets that match the configured rules are allowed through. For example, a rule could allow TCP traffic on port 80 while blocking other ports. Carefully configured rules optimize security while allowing desired connections.
Windows provides inbound rules to control incoming traffic and outbound rules to filter outgoing traffic. Rules can be tailored for each network profile.
Windows Firewall with Advanced Security
Windows Firewall with Advanced Security provides the management interface for configuring Windows firewall settings. It comes built-in to Windows Server without needing additional licensing or hardware.
There are three default firewall profiles:
- Domain – For corporate networks with detected domain controllers
- Private – For home or office networks behind a gateway device
- Public – For untrusted public networks with internet access
Profiles allow custom rules per network type. You can enable, disable, or configure profiles independently.
Accessing the Firewall Console
To open the Windows Firewall with Advanced Security console:
- Open Server Manager > Tools > Windows Firewall with Advanced Security
- Search for “firewall” in the Start menu and launch the Windows Firewall shortcut
- Run wf.msc in the Run command (Win + R)
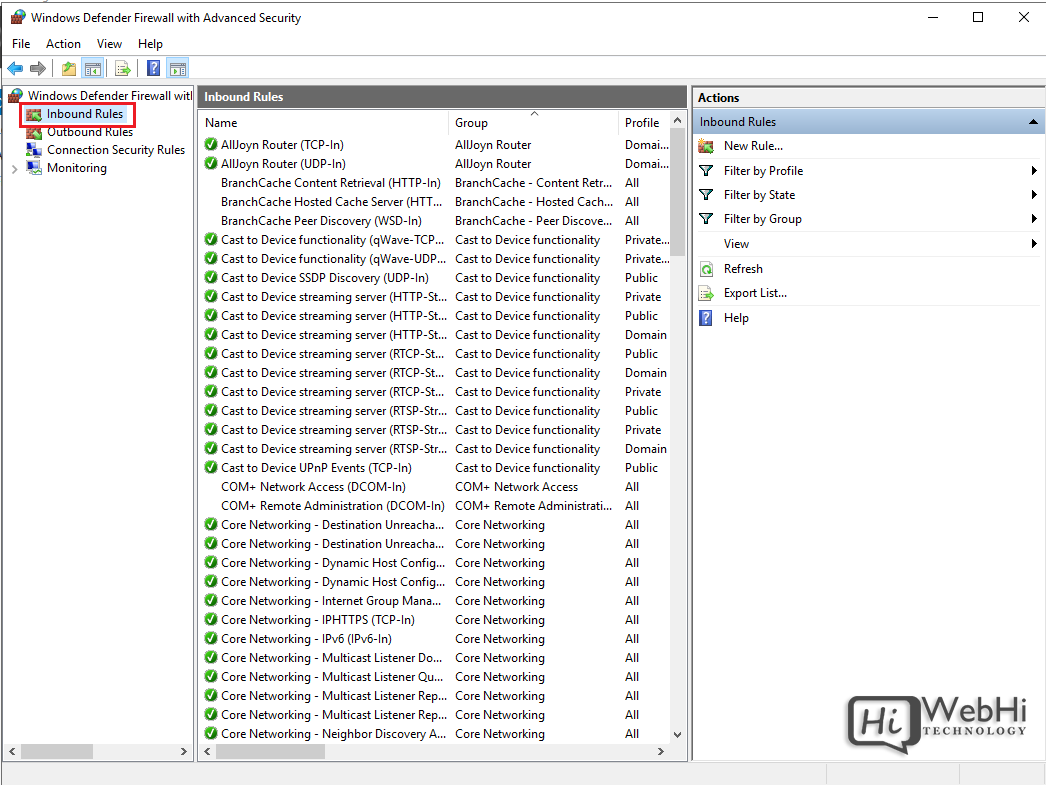
The left menu allows configuring inbound rules, outbound rules, connection security, and monitoring.
Configuring Firewall Rules
Firewall rules control whether to allow or block specific network connections. Rules can filter by:
- Program path
- Port and protocol
- Predefined service
- Source/destination IP
- Network interface
- And more…
Follow these steps to create an inbound firewall rule:
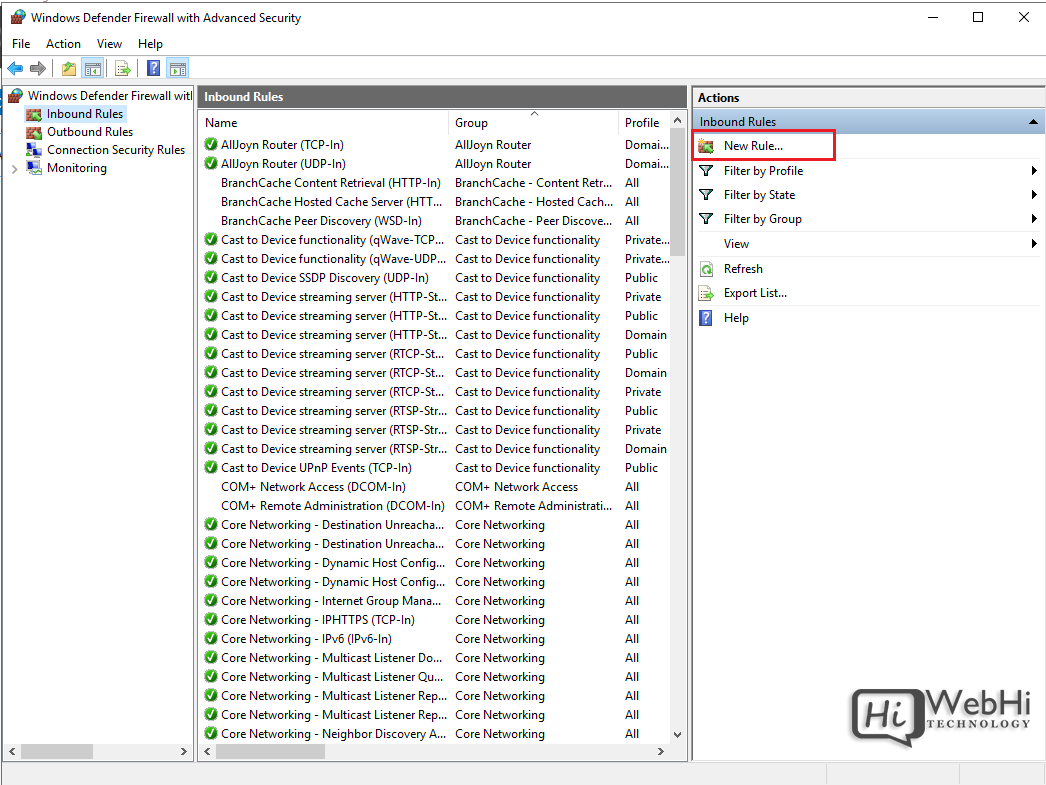
1. Open the Firewall console and select Inbound Rules
2. Click New Rule to launch the rule wizard
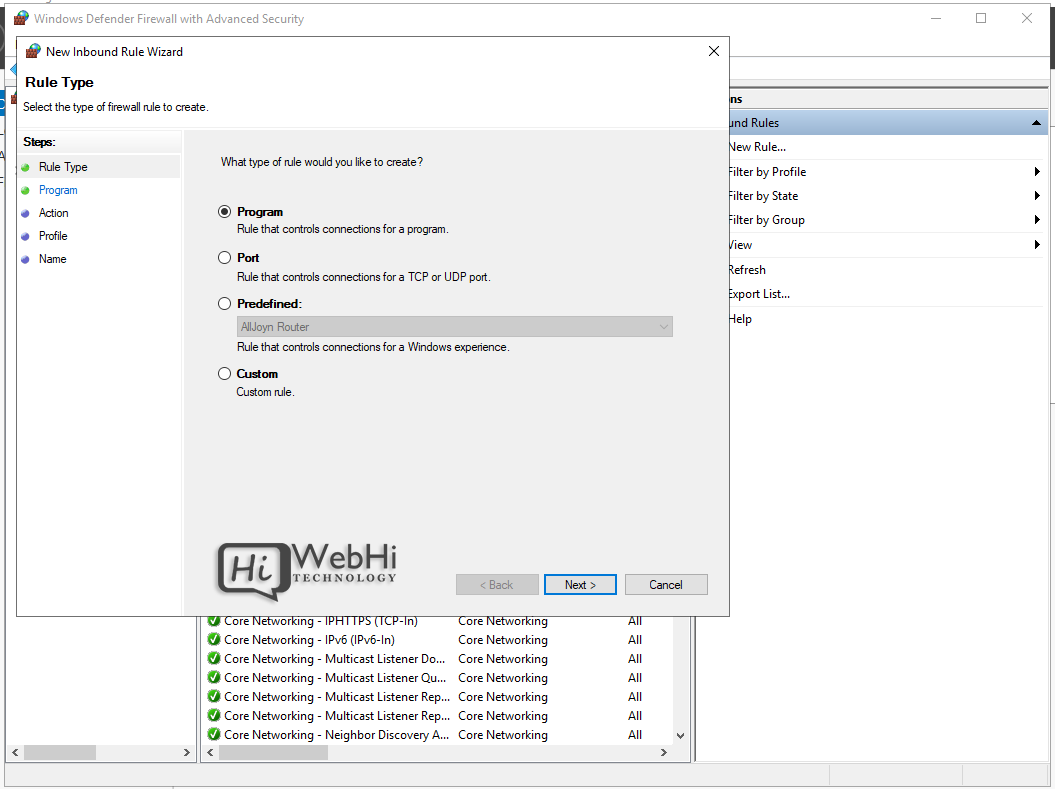
3. Select the rule type – Program, Port, Predefined, or Custom
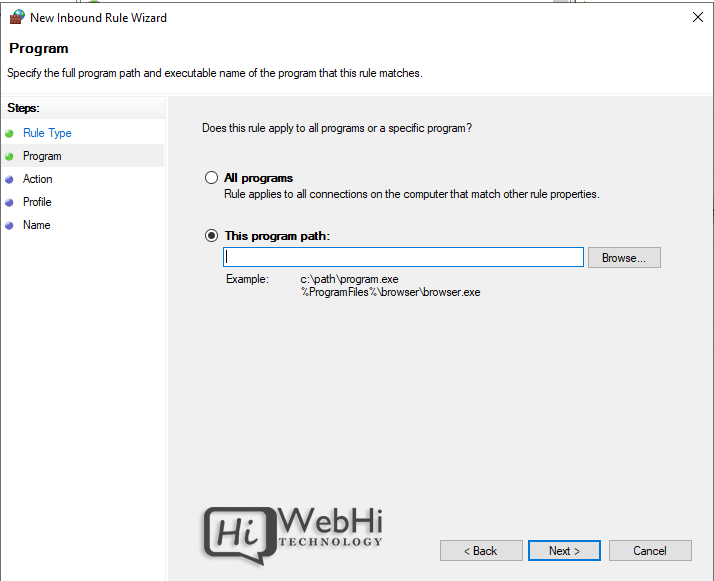
4. Choose All Programs or a Program path
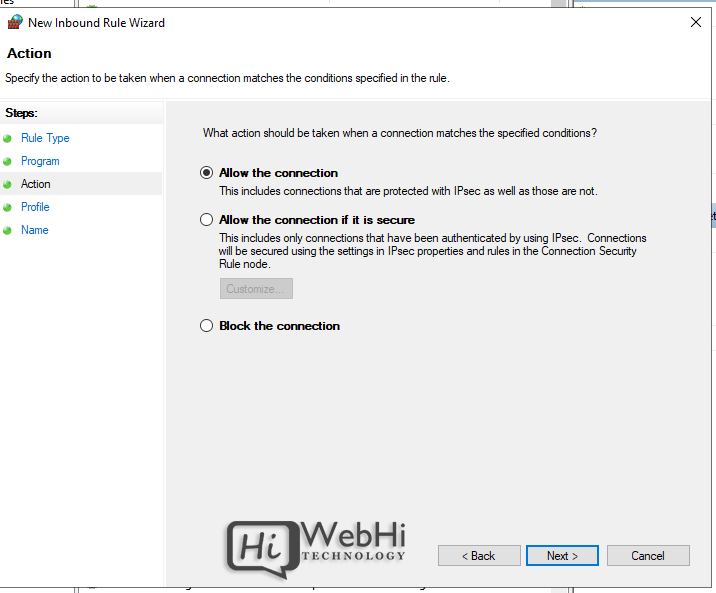
5. Choose Action (allow or block) or allow if connection is secured
6. Choose profiles
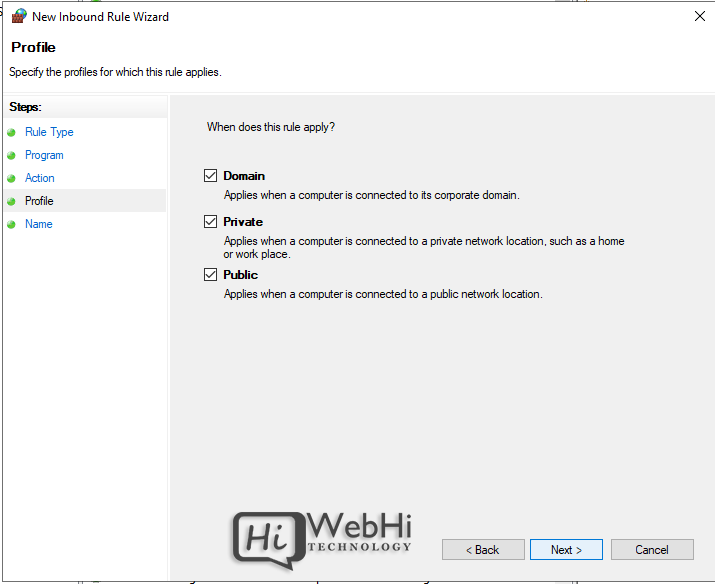
7. Name the rule and click Finish
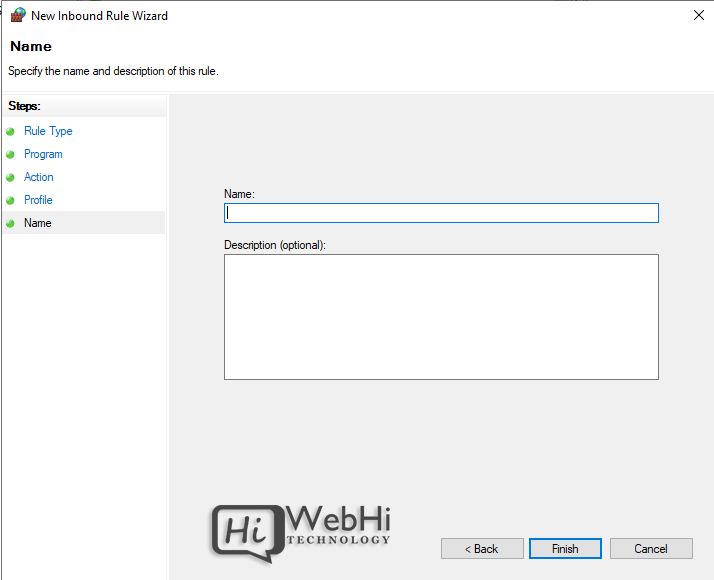
Repeat the wizard for outbound rules. Once created, rules can be edited or disabled from the console.
Rules can also be created from PowerShell. For example:
PS C:\Users\Administrator> New-NetFirewallRule -DisplayName "Allow SSH" -Enabled True -Direction Inbound -Action Allow -Protocol TCP -LocalPort 22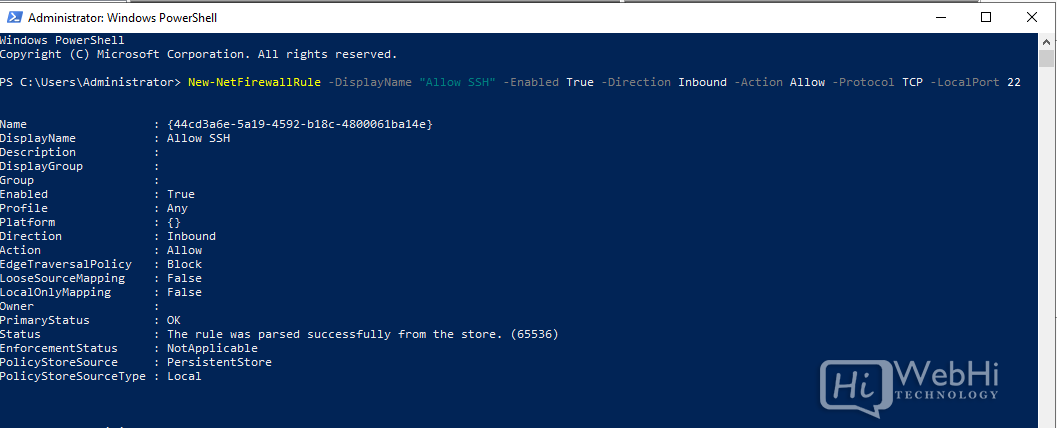
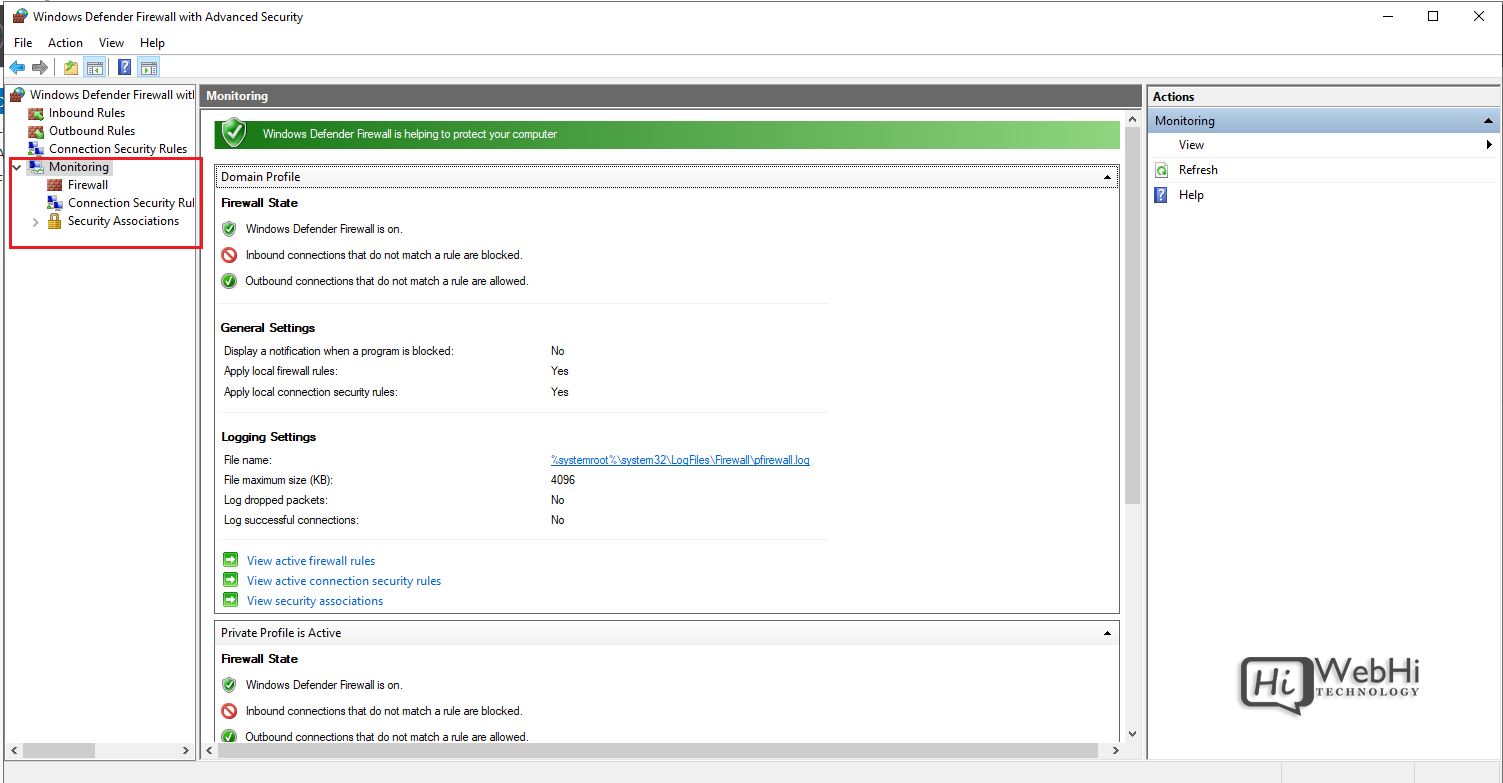
Monitor active connections under the Monitoring tab.
Conclusion
The Windows Firewall provides a flexible and granular rule-based firewall solution for Windows Server 2016, 2019 and 2022. The advanced interface allows creating detailed rules to filter incoming and outgoing traffic as needed. Monitor activity to verify your rules are working correctly. Careful configuration enhances security while allowing desired connections.
